IT Department Warns Students of E-Mail Phishing Scam
 Two waves of e-mails blasted to over 14,000 University members have been deemed a “harmful phishing scam,” according to Robert Carsey, Director of Server Operations. It is reported that at least 50 student mailboxes were compromised by the scam.
Two waves of e-mails blasted to over 14,000 University members have been deemed a “harmful phishing scam,” according to Robert Carsey, Director of Server Operations. It is reported that at least 50 student mailboxes were compromised by the scam.
The e-mails told recipients to update their eCampus log-in information using an attached link, posing as a University-affiliated source.
The University has since urged the campus community to delete the e-mails, report any instances of opening the scam to the IT Help Desk, and change all Monmouth-related passwords for security measures.
Carsey stated that employees began receiving the first wave of e-mails on Friday, Jan. 26 at approximately 1:15 p.m., with the first Help Desk request regarding the e-mail being submitted at 1:22 p.m.
Only minutes later, the IT team began mitigating the blast. The mitigation attempts included deleting the e-mails from users’ mailboxes, blocking the link on the University’s firewall, and notifying users. The mitigation process for the first wave of e-mails was completed by 2:00 p.m. that day.
“We didn’t give the phishing attempt much credit because the e-mail itself was rather unenticing and our employees are generally very good at not responding to such attempts,” said Carsey. “Combined with the fact that we removed the email quickly, we were satisfied this was contained. However, we took the unusual step of notifying employees because this was the first time a phisher had copied our real University login page.”
The second wave of e-mails began on Saturday, Jan. 27 at approximately 10:49 a.m. According to Carsey, the phisher obtained the login credentials of an account and logged in, and then sent the scam e-mail to all student mailboxes.
“Since [the second wave] was an internal Monmouth-to-Monmouth e-mail, there was no limit to the number of e-mails that could be sent, nor was it scanned for malicious links,” Carsey said. According to Carsey, they began the process of removing the e-mail from all accounts at 11:24 a.m. However, due to the amount of mailboxes targeted, the process took “some time.”
“Phishing is a scheme of deception where an attack that is intended to look legitimate to purport individuals into revealing sensitive information like a password regarding the targeted website,” said Jordan Vashey, a senior homeland security student who works with cyber security at the company CyanLine.
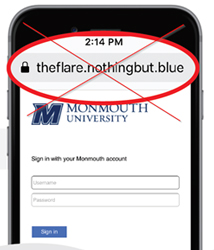 According to Vashey, in phishing scams attackers generate a template identical to the target system. In this case, the targeted system was the Monmouth University eCampus site. The templates, which can be used in e-mails by using hypertext markup language (HTML), can be duplicated and hosted on the hacker’s system.
According to Vashey, in phishing scams attackers generate a template identical to the target system. In this case, the targeted system was the Monmouth University eCampus site. The templates, which can be used in e-mails by using hypertext markup language (HTML), can be duplicated and hosted on the hacker’s system.
“If an attacker duplicated the eCampus template and hosted it on their system, e-mails can be sent out that look exactly like a staff member or professor at Monmouth,” Vashey explained. “The target would then click a link in the e-mail that would redirect the user to the duplicated Monmouth University eCampus login. The user logs in, and it may even redirect you to the real eCampus and log in, making everything look perfectly normal.”
According to Carsey, at least 50 student mailboxes have sent out junk mail e-mails, meaning that they have been compromised by the phishing scam.
“We have no way of knowing who clicked on the malicious link and gave their credentials to the phisher,” Carsey said. “However, we can see when an e-mail account sends out junk mail. For those accounts, the ability to send mail is automatically blocked after 100 [junk] messages, administrators are notified, and we administratively change that user’s password. While immediately changing passwords on an account presents additional problems, it’s necessary to avert more serious problems.”
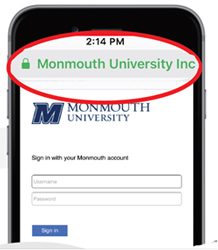 On Thursday, Feb. 1, an e-mail was sent to faculty warning them of the e-mail, pointing out that Monmouth student accounts had been compromised.
On Thursday, Feb. 1, an e-mail was sent to faculty warning them of the e-mail, pointing out that Monmouth student accounts had been compromised.
According to Carsey, the only repercussions of this event have been spam emails sent from University accounts. However, in other cases, online scammers have made attempts to access employee or student worker W-2 information, which includes addresses and Social Security numbers; other scams have attempted to deregister students from classes or send threatening e-mails to politicians.
Carsey also warned that students who use the same password for their Monmouth account and other accounts could see those other accounts compromised.
“Your username and password was logged when your browser performed a POST function to send your login to the databse to verify whether it is the correct login information or not,” said Vashey. “Now the attacker has your password, and is free to use [it] at their discretion.”
“I’m not worried about my personal information being affected, because there really isn’t a relationship that allows the information of one student to access the information of other students,” said Harry Torrenegra, a graduate student studying software engineering who received the e-mail but did not click on the spam link. “They’re all sectioned off from one another.”
According to Carsey, these e-mails are not unusual for the University to receive. However, multiple layers of security mean that 70 percent of spam e-mails are blocked from reaching University servers.
“Incidents such as this one prompt us to review our processes and mitigation strategies. To date, several changes have been made and several more are being tested,” Carsey added. “Securing our systems, and ensuring the integrity of our data, is a continual process that must match the tenacity of those trying to gain unauthorized access.”
Carsey emphasized the importance of students being careful about what they click on in case of scams. While the current phishing scam e-mail was moved to the “Deleted Items” folder of student emails, there is still a risk of similar scams in the future.
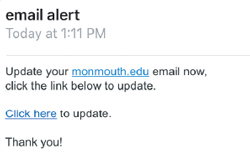 According to Carsey, some of the most obvious hallmarks of a scam e-mail is the poor composure, alternate or incorrect spellings, and incorrect links.
According to Carsey, some of the most obvious hallmarks of a scam e-mail is the poor composure, alternate or incorrect spellings, and incorrect links.
“Most phishing e-mails are poorly composed or use alternate spellings of words that we don’t use here in the U.S.,” Carsey explained. “These are easily recognized and ignored by most people. In the current instance, the phishing e-mail was very short, didn’t provide much context, and provided a link that appeared to take you to the Monmouth login page. It was the perceived legitimacy of the fake log-in page that seemed convincing.”
Carsey recommended double-checking the URL of a site before entering credentials or personal information to confirm that it belongs to the company that is sending the e-mail.
“If there is any doubt about the legitimacy of an e-mail or link, please contact the Help Desk for help,” Carsey stated.
PHOTO TAKEN by Nicole Riddle
PHOTOS COURTESY of Robert Carsey


