Two more waves of phishing scam e-mails were sent to both students’ accounts, and student organization accounts over the span of two days, starting April 5 at approximately 7:07 p.m. and ending April 6, at about 8:54 p.m.
Robert Carsey, Director of Server Operations confirmed that the emails were in fact a scam. Janine Frederick, a systems administrator at Server Operations, was responsible for taking care of mitigating the most recent round of spam e-mails affecting the students.
Frederick reported that while the exact number of student accounts reached is not known, it was certainly in the thousands.
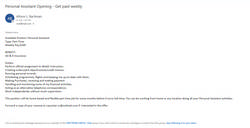
The e-mails informed recipients of a possible part-time job opening as a personal assistant, and included details such as weekly pay, benefits, requirements for the position, and details regarding what the position entailed. The e-mail concluded by asking recipients to forward a copy of their resume to raycarter.rc@outlook.com. The e-mail came from multiple accounts, posing as student email accounts.
Frederick explained how these e-mails were able to breach student accounts. “In every case where unauthorized access is gained to an MU e-mail account, it is the result of a user providing his/her login information during a phishing scheme. That login information is later used to access the user’s e-mail account to send spam or scam messages,” she said.
Lauren Niesz, a graduate student of management information studies, explained that the phishing scam used a technique called masking, where e-mails are routed to a different account of the person accountable for the scam, and the actual link to the e-mail address is visible, but often overlooked, especially by students who trust that their e-mail accounts are safe. In some cases, the accounts are realistic but they’re not the real thing. I got it on my club’s e-mail, so student e-mails and club e-mails were definitely affected by it. It is vicious that people do this, but so easy unfortunately,” she said.
Frederick also gave an explanation for the source of the spam e-mails. “The e-mails were sent from compromised student accounts to other student accounts,” she continued. “Information Management was unaware that the e-mail accounts had been accessed by anyone other than the appropriate user until others began receiving and subsequently reporting the scam messages.”
Steps were taken as soon as Information Management was made aware of the problem, according to Frederick. After a brief investigation, accounts used to send the emails were disabled, and information to filter these e-mails was added to their SPAM and malware filters to prevent reoccurrence.
On Monday, April 16, Career Services alerted students to the scam with an e-mail that read, “We have reason to believe this job posting is a scam and may result in economic loss for any student that applies. Although this job posting did not originate with Career Services, we are making this announcement as a public service. If you receive this job posting in the mail, ignore it and delete it.”
Niesz explained what could potentially happen if a student were to actually forward their resume or personal information to the scam account.
“The e-mail would be routed to a different account of the person accountable and they’d respond using the same pseudo e-mail asking for more information,” Niesz said. “It could potentially stem into them saying they’d do an advanced payment to them for their first month of work or so and they’d get banking information and would be able to take funds out of the account. That is just one likely scenario.”
KerryAnn De Meester, a software engineering student, explained that people should know about these scams because they are such a common form of information stealing. “Basically this is a phishing scheme so the scammers’ goal is to get the student to give up personal information….and ultimately can result in some form of identity theft.”
DeMeester added that there are many ways for scam e-mails to infiltrate student e-mail addresses. “Some spammers actually buy information that includes e-mail addresses from other companies (which is illegal). Some have programs to auto generate e-mails that end with @ and then any website. In this situation, I believe that affected students used their e-mail addresses with untrustworthy websites,” she explained. “This could happen in any number of ways such as allowing third part apps to access your information through Facebook, for example, so the scammers could have obtained student information from the student involuntarily.”
“E-mails such as this one seek to gather access to accounts, personal information or initiate an action such as sending a check or buying gift cards,” Frederick added. “Armed with this information, fraudulent purchases, identity theft and other fraudulent actions can be taken.”
In February, a similar phishing attack occurred where student e-mails were compromised after receiving an e-mail to update their ecampus login. This scam has since urged the University to crack down and pay closer attention to any other attempts that might occur.
In response to that offense, Frederick explained that Information Management takes attacks to the University’s account security seriously, retaining services from Microsoft and Barracuda to secure the Monmouth e-mail.
“We remain vigilant in mitigating any and all attacks or attempts to infiltrate accounts. Cybercriminals are often sophisticated in how they craft their emails to avoid detection by services designed to filter out these e-mails,” Frederick said. “However, our efforts can only be successful when users bring suspicious emails or unauthorized access attempts to our attention as it allows us to act quickly.”
The University advised the campus community to delete the e-mails, report any instances of opening the scam to the IT Help Desk, and change all Monmouth-related passwords for security measures, however since February it seems that that those efforts have been thwarted, but through no fault of the University, according to DeMeester. “There’s no way any software can stop every single breach. Therefore, a student should be informed of these types of attacks and how to spot them,” she said.”
“Any e-mail requesting personal information should raise a red flag. Students should also check the return address. In this case, the return address was mail@mail, which is definitely sketchy.”
Information management urges all students to report possible spam emails to the Help Desk at (732) 923-4357 (HELP), and offered that there are resources available to ensure awareness and protection.
There are resources available on the University’s website to help students identify e-mail and phishing scams.
PHOTO TAKEN by Kerry Breen